Purpose:
The purpose of this article is to show how to audit the Event logs for File Delete operations. We will use XPath to filter for the Delete event inside the Event Data level of the XML detail.
Solution:
Step1: Enable file auditing from Group Policy Object. We will refer to it as GPO from here.
Open Group Policy Management.

Create a new GPO in the Organization Unit (OU) that you will want to enable for file auditing. In this case we will use the Root of the domain to apply to all computers.
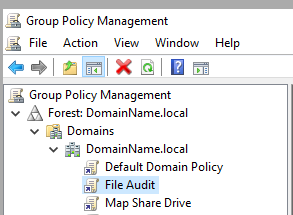
In the Group Policy editor, click through to Computer Configuration -> Policies -> Windows Settings -> Local Policies. Click on Audit Policy.
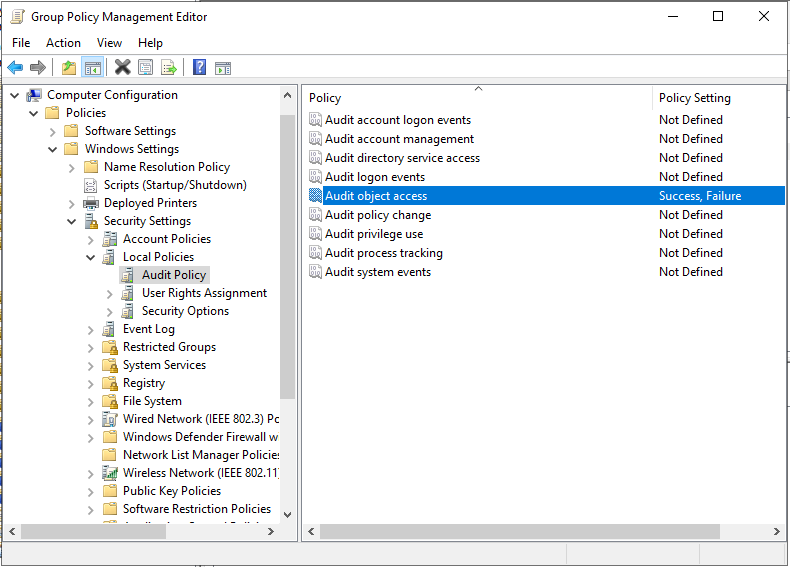
To enable your new GPO, go to a command line and run ‘gpupdate /force’.
Step 2: Apply Audit Policy to Files and/or Folders.
This will tell Windows exactly what events we would like to audit.
Right-click the file or folder in Windows Explorer. Select Properties.
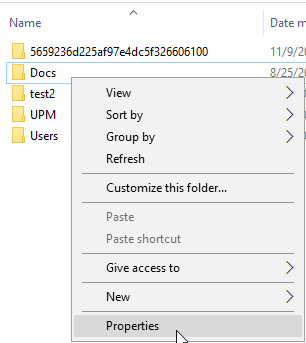
Click on the security tab -> Advanced
Click on the Auditing tab -> Continue.
Click on Add
Select a Principal login name to audit. (In this case we will use the Domain Users Group.)
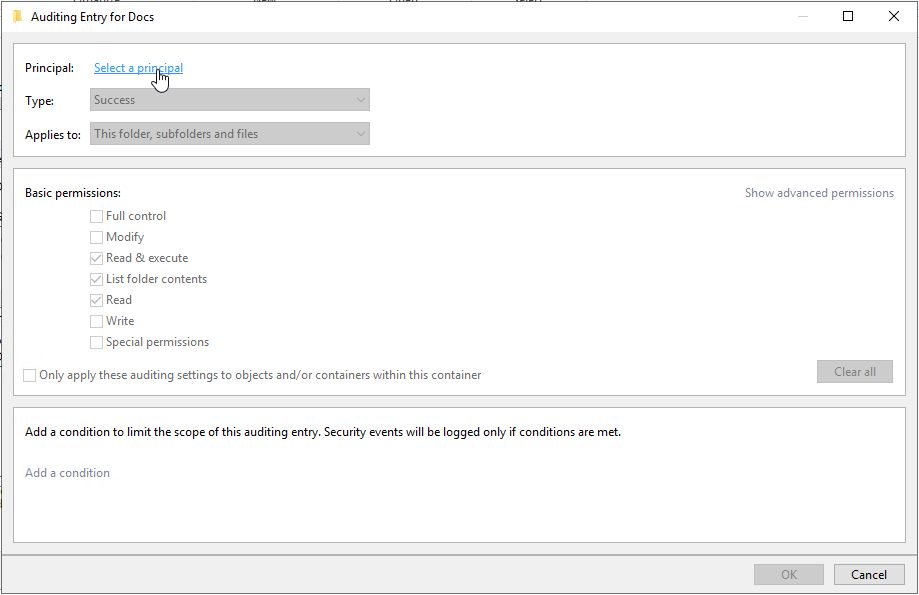
Select the events to audit for. To not bloat the security event log we will select Create files / write data, Create Folders /append data, and Delete.
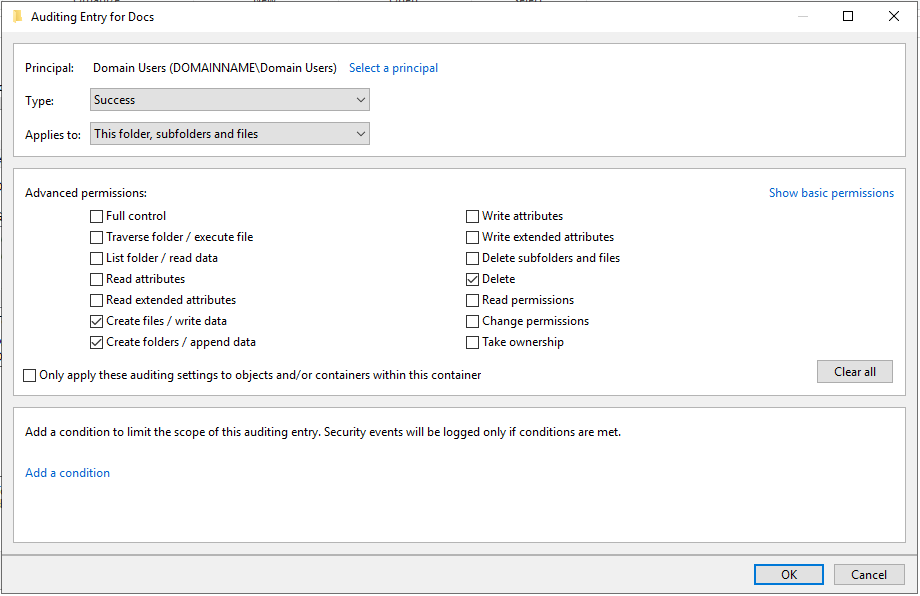
At this point we will start to see events for file access. Event ID 4663
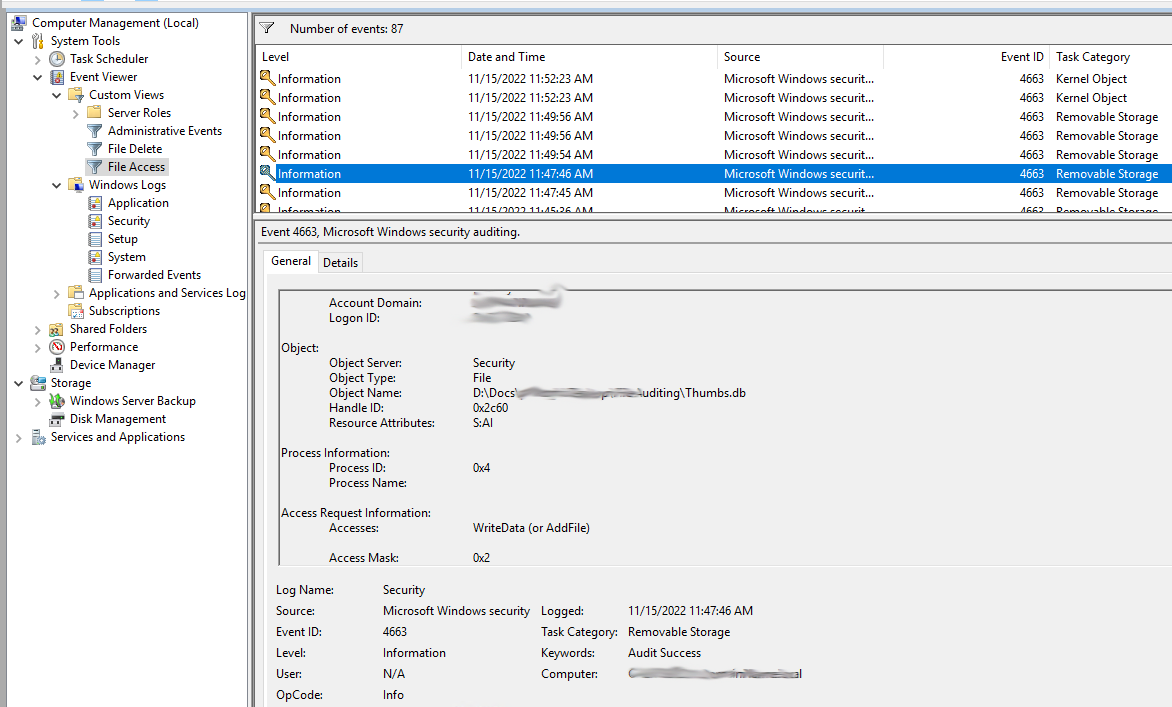
The following table provides more information about each event:
| Event ID | Name | Description | Data it provides |
| 4656 | A handle to an object was requested |
Logs the start of every file activity but does not guarantee it succeeded | The name of the file SubjectUserName Process Name |
| 4663 | An attempt was made to access an object | Logs the specific micro operations performed as part of the activity | What was done with the object |
| 4660 | An object was deleted | Logs a delete operation | Object was deleted Security ID (User) Handle ID only (This event doesn’t contain the name of the deleted object) |
| 4658 | The handle to an object was closed | Logs the end of a file activity | How much time it took Security ID Process Name |
Event ID 4660 logs a delete operation, but does not tell us what file was deleted
Step 3: Create a filter for Event ID 4663
In the event viewer click on Custom Views -> Create Custom View …
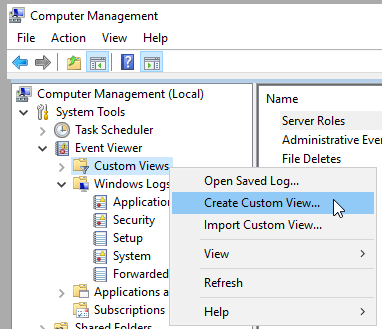
Click the Checkbox for Critical, Warning, Verbose, Error, and Information. Select the Security log under Event Logs. Enter the ID 4663 for the Event ID.
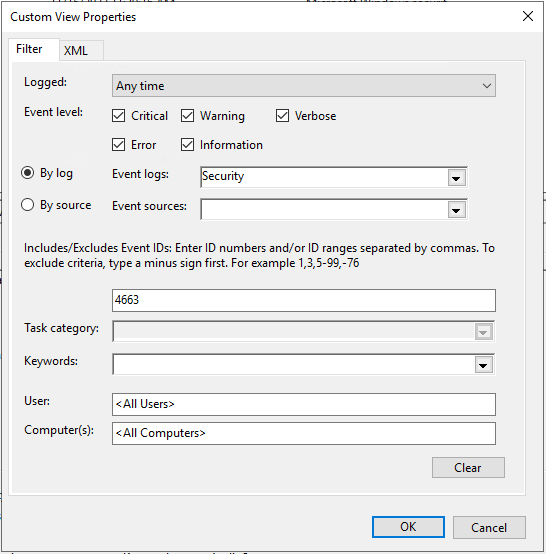
Name the Filter File Access.
This filter will now show us Events for Event ID 4663.
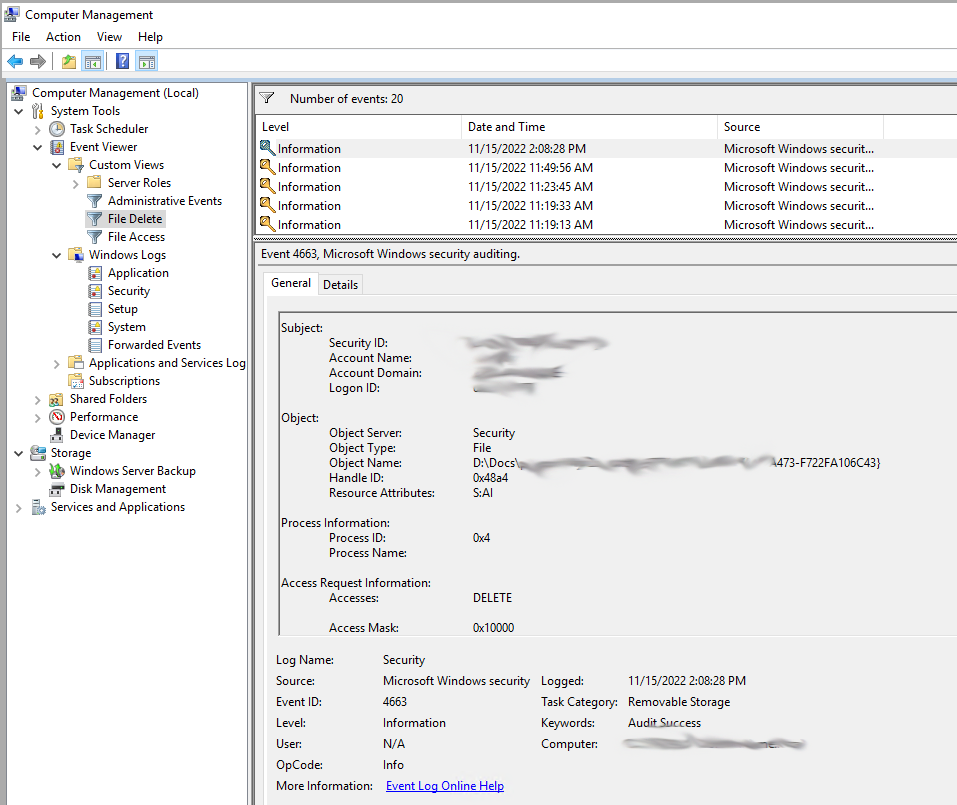
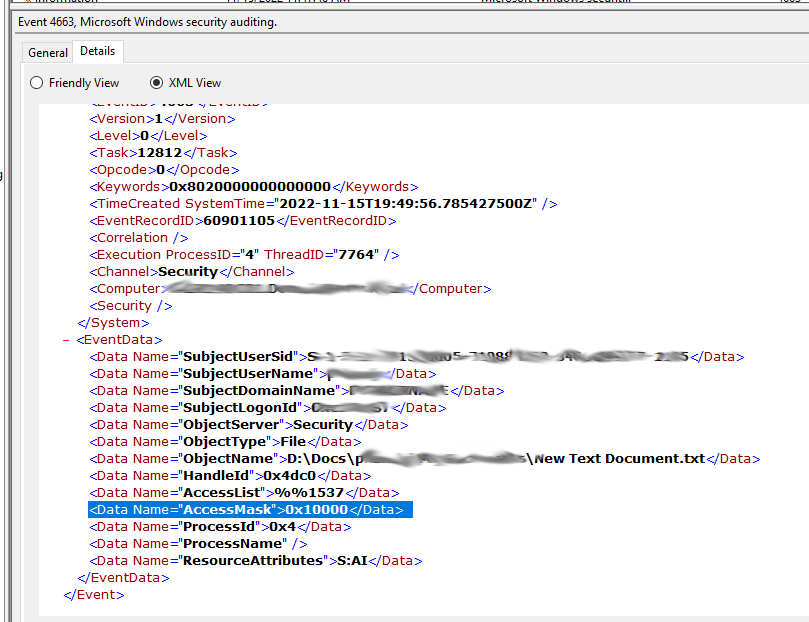
We are interested in the Delete Micro Operation for this event ID. Access Mask 0x10000.
Because this is not something we can get from the GUI filter we will need to make a custom filter in XPath form.
Step 4: Create a Custom make a custom filter in XPath form to View Deleted Files
Right Click on Custom Views -> Create Custom View...
Click on the XML tab
Click the Check mark to Edit query Manually and enter
<QueryList>
<Query Id="0">
<Select Path="Security">
*[EventData[Data[@Name='AccessMask'] and (Data='0x10000')]]
and
*[System[(EventID='4663')]]
</Select>
</Query>
</QueryList>
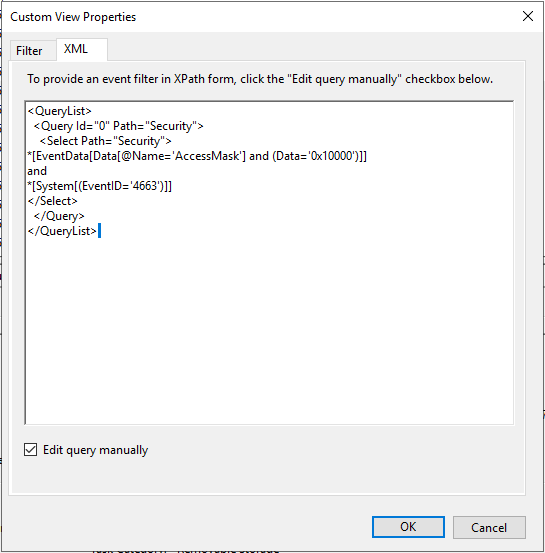
We are now using an event filter in XPath form to filter events for the Delete operation.

This technique can be used to filter for the rest of the AccessMask operations.
| Access | Hex Value, Schema Value |
Description |
| ReadData (or ListDirectory) (For registry objects, this is “Query key value.”) |
0x1, %%4416 |
ReadData - For a file object, the right to read the corresponding file data. For a directory object, the right to read the corresponding directory data. ListDirectory - For a directory, the right to list the contents of the directory. |
| WriteData (or AddFile) (For registry objects, this is “Set key value.”) |
0x2, %%4417 |
WriteData - For a file object, the right to write data to the file. For a directory object, the right to create a file in the directory (FILE_ADD_FILE). AddFile - For a directory, the right to create a file in the directory. |
| AppendData (or AddSubdirectory or CreatePipeInstance) | 0x4, %%4418 |
AppendData - For a file object, the right to append data to the file. (For local files, write operations will not overwrite existing data if this flag is specified without FILE_WRITE_DATA.) For a directory object, the right to create a subdirectory (FILE_ADD_SUBDIRECTORY). AddSubdirectory - For a directory, the right to create a subdirectory. CreatePipeInstance - For a named pipe, the right to create a pipe. |
| ReadEA (For registry objects, this is “Enumerate sub-keys.”) |
0x8, %%4419 |
The right to read extended file attributes. |
| WriteEA | 0x10, %%4420 |
The right to write extended file attributes. |
| Execute/Traverse | 0x20, %%4421 |
Execute - For a native code file, the right to execute the file. This access right given to scripts may cause the script to be executable, depending on the script interpreter. Traverse - For a directory, the right to traverse the directory. By default, users are assigned the BYPASS_TRAVERSE_CHECKING privilege, which ignores the FILE_TRAVERSE access right. See the remarks in File Security and Access Rights for more information. |
| DeleteChild | 0x40, %%4422 |
For a directory, the right to delete a directory and all the files it contains, including read-only files. |
| ReadAttributes | 0x80, %%4423 |
The right to read file attributes. |
| WriteAttributes | 0x100, %%4424 |
The right to write file attributes. |
| DELETE | 0x10000, %%1537 |
The right to delete the object. |
| READ_CONTROL | 0x20000, %%1538 |
The right to read the information in the object's security descriptor, not including the information in the system access control list (SACL). |
| WRITE_DAC | 0x40000, %%1539 |
The right to modify the discretionary access control list (DACL) in the object's security descriptor. |
| WRITE_OWNER | 0x80000, %%1540 |
The right to change the owner in the object's security descriptor |
| SYNCHRONIZE | 0x100000, %%1541 |
The right to use the object for synchronization. This enables a thread to wait until the object is in the signaled state. Some object types do not support this access right. |
| ACCESS_SYS_SEC | 0x1000000, %%1542 |
The ACCESS_SYS_SEC access right controls the ability to get or set the SACL in an object's security descriptor. |